EPFL IC Research Day 2019/06/06
=
The event https://icresearchday.epfl.ch/ with all the slides in PDF and the videos of the talks.
Notes by Maria Dimou
Photos by Mary Georgiou
## Summary for busy people
This cartoon (shown by the EPFL President during the Welcome talk) with Zuckerberg hugging facebook newcomer while stealing the addressbook and wallet from _her_ (again!) backpockets gave the impression that the day starts well.
Unfortunately, the rest was not at the level of [the 2013 EPFL Congres on Privacy and Surveillance](https://memento.epfl.ch/event/congress-on-privacy-surveillance/), which remains unforgettable for me, please have a look at the speakers!...
These notes are not complete. They just contain some keywords that can be used for searching.
The offline discussions in front of the posters were most interesting. If one wishes comfort then privacy is sacrificed. If one wishes not to be profiled and previous searches not to be stored, then irrelevant results will come up for ever.
## M.Veterli -EPFL President
Smaky: 1974 PC made at EPFL
2018: Computational Thinking (new course)
50 years of EPFL (celebration)
facebook: 2.5 M users
## Jim Larus - IC Dean
EPFL 8th in the World University ranking this year. (ETHZ is 9th)
78+ EdTech Collider (a collection of startups in the area of Education)
Extension School (10 courses that provide certificates)
## Jean-Pierre Hubaux
Some brief mention of Ideology and Identity in the work of [Francis Fukuyama](https://en.wikipedia.org/wiki/Francis_Fukuyama) (are western world right forever? book)
NSA leaked cyberwar sw EternalBlue , created byproducts like WannaCry and NotPetya
c4dt.org centre of digital trust - EPFL founded
## Dan Wallach - Rice Univ.
E-voting systems: Internet NO, paper contains fear of purchased or threatened voters, ambiguity about the voter’s intention and scanning devices’hacking, dedicated specifically invented machines ok but the bar codes don’t necessarily match the voter’s intention. Nevertheless, electronic parsing of the votes is mandatory due to US legislation on Disabilities (all people with any disability should be able to vote). Going to voting venues can be considered a risk in the USA because of guns etc
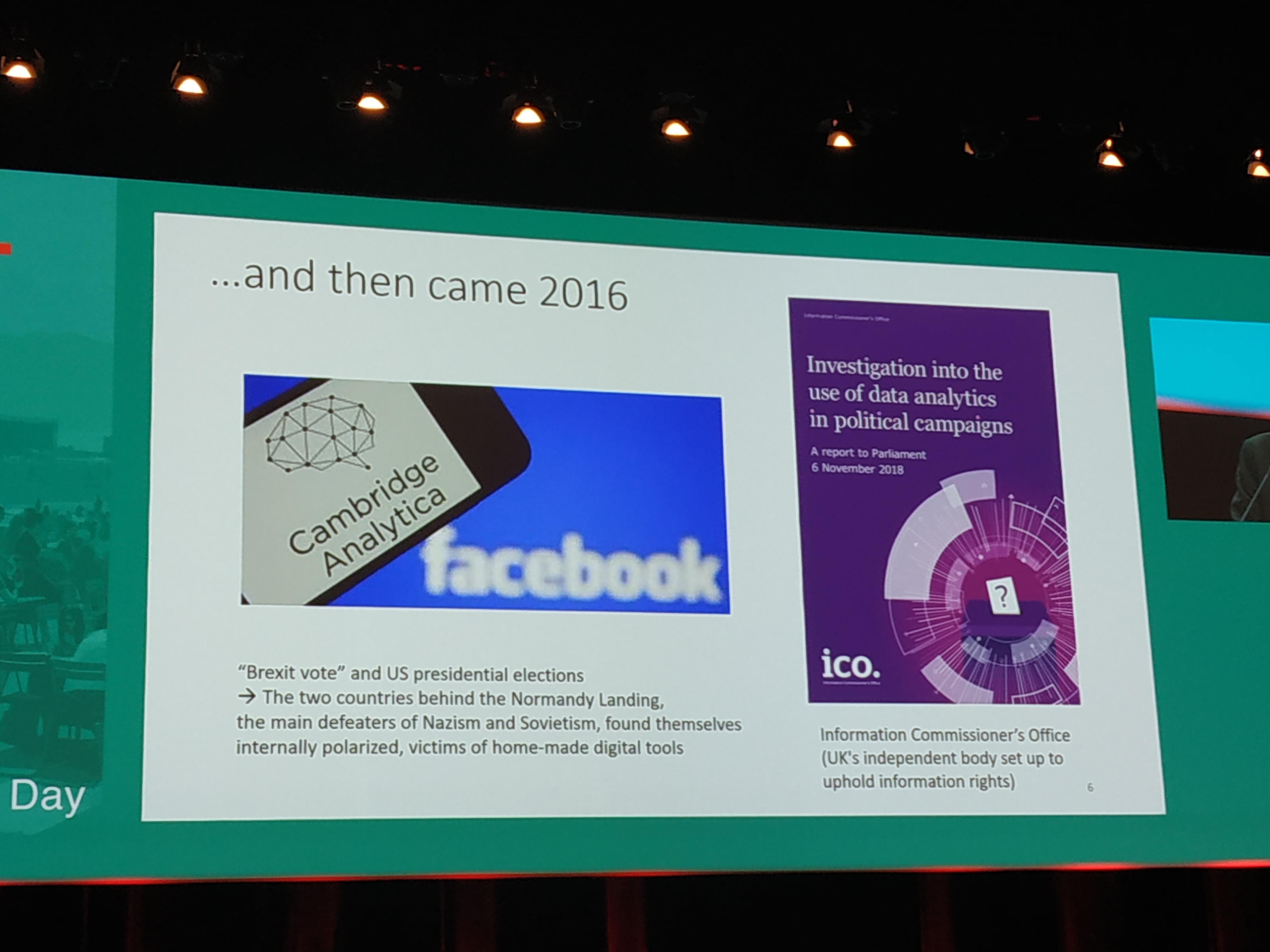
The fear of information manipulation.
## Carmela Troncoso - EPFL
Adversarial ML: About the impact of ML in health and advertising. Adversarial advertisement engineers images to alter their identification and prevent the product from being retrieved in searches.
Following the chinese “Art of War” book ‘to win your enemy you have to become your enemy’ develops graph-theory-based techniques to ‘act’ as an adversary (by buying ‘friends’, ‘likes’ etc). They try to modify the user’s data BEFORE they enter the machinery that can feed inference. They throw fake info in the net so that the advertisement exploration get the wrong idea about potential customer preferences.
To fight social injustice they use ‘Robin Hood’ intermediates, for ex. to people who can’t obtain loans.
## Lightning Talks - 10 students
Vote via QRCode
compare model image with actual parsed road image and alert self-driving car for discrepancies.
presenve user’s privacy by protecting the metadata of encrypted messages.
who-is-th.at recognising a person from an image by presenting multiple images, asking the user to choose and narrowing down the result.
## Mathias Payer - EPFL
hexhive.github.io research group Open Source code.
Google Chrome 76MLoC (Lines of Code)
Linux OS 17MLoC
Projects T-Fuzz, RetroWrite, USBFuzz: Because of the vast amount of LoC and distributed developers’ community they develop ‘defences’ that simply raises a lot the cost of attacks. For code sanity they try to identify NCC (Non Critical Checks), drop them and save time. For ex. an ‘if’ statement that is never satisfied due to previous constrains, is simply removed. They work with C/C++ code but they can only evaluate for quality other programming languages.
They also try to sanitise binary-only code (no access to source) by retro-writing. They create assembly code from the binary and then re-compile to re-obtain a new (identical?) binary.
They also do peripherals’ testing, e.g. USB interfaces. Their stack was written in the mid-1990ies, when the attacks were different/simpler…They found 60 vulnerabilities out of which 34 were severe for the Linux kernel. Linus Torvalds agreed that this team joins Linux kernel development to fix these vulnerabilities.
## Ari Juels - Cornell
Connected via Skype. The most interesting talk of the day. About cryptocurrencies. Just watch the video [from this page](https://icresearchday.epfl.ch/#speaker).

